Email Cyber Security Guard
Email Cyber Guard enhances built-in security capabilities to address inbound threats and outbound data loss risk
Web Cyber Security Guard
cloud-based Web
Security Guard offers protection against online security threats by enforcing security policies and filtering malicious internet traffic in real-time.
Email Cyber Security Guard
Most complete email protection and visibility
Stop ransomware and other threats
Forcepoint Email Cyber Security uses the Advanced Classification Engine (ACE) to identify threats ranging from annoying spam to advanced malware, phishing, and Business Email Compromise (BEC) attacks.
Stop ransomware and other threats
Advanced capabilities detect data theft concealed in images or custom-encrypted files, even when gradually transmitted in small amounts to evade detection.
Control device access to email attachments
Prevent total access to sensitive email attachments on vulnerable unmanaged devices (BYOD) while permitting full access to secure managed devices.
Ensure confidentiality of sensitive communications
Enable secure delivery of email communications with Forcepoint Email Encryption that eliminates the traditional barriers of cost and complexity by offering easy administration, without key management or additional hardware.
Identify explicit images to enforce acceptable use
The Forcepoint Image Analysis Module allows employers to proactively monitor, educate, and enforce company email policy for explicit or pornographic image attachments.
Spam and phishing protection
Detect unwanted spam and unsafe phishing emails, allowing customers to block, quarantine, or take other actions.
TheVoipShop offers full protection through Forcepoint, a highly reliable, scalable and richly featured Cloud-based email and web security service.
Optimum value comes from effective, holistic email security
Get both maximum effectiveness and return on investment (ROI) with Forcepoint Email Security. Read the report.
100%
99%
6
The Forcepoint Email Security advantage
Real-time threat protection
Real-time threat protection uses a unique blend of detection technologies, including machine learning, sandboxing, and predictive analytics to effectively stop advanced threats such as ransomware.
Powerful encryption for additional protection
Encrypt sensitive email conversations and enhance mobile security by controlling sensitive attachments access by device.
Integrated data loss prevention
Integrated industry-leading data loss prevention stops data infiltration and exfiltration capabilities.
Complete out-of-the-box solution
Forcepoint Email Security includes DLP, URL wrapping, and other capabilities that are considered premium "add-ons" or upgrades by many competitors, delivering the most comprehensive inbound and outbound defenses out of the box.
Protection against highly evasive zero-day threats
Get advanced malware detection (sandboxing) with our full system emulation sandbox. Deep content inspection reveals highly evasive zero-day threat with no false positives.
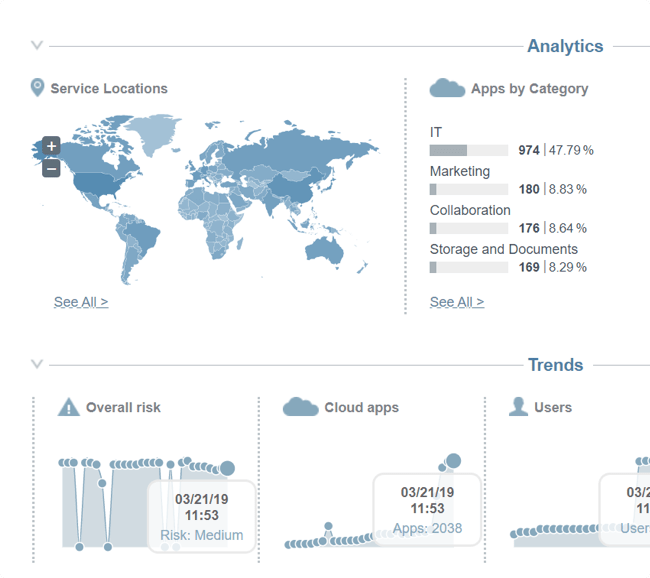
Incident risk ranking to find the greatest risks
Incidents are correlated across multiple events to identify true cumulative risk trends and activity. A risk score is included to help security teams identify the greatest risks based on real-time activity.
Unique phishing education feature
Use Forcepoint Email Security’s unique phishing education features to help users adopt best practices and identify those who need additional training to improve their security awareness.
Deployment flexibility
How you deploy our email security solution is up to you. Choose from a range of physical and virtual appliances to leverage existing hardware, cloud deployment, or hybrid environments.
Web Cyber Security Guard
Making the web safe for the global enterprise.
Any device, any cloud, any app
Behavioral analytics and inline capabilities secure your policies and data across the world.
Safe access for every user, anywhere
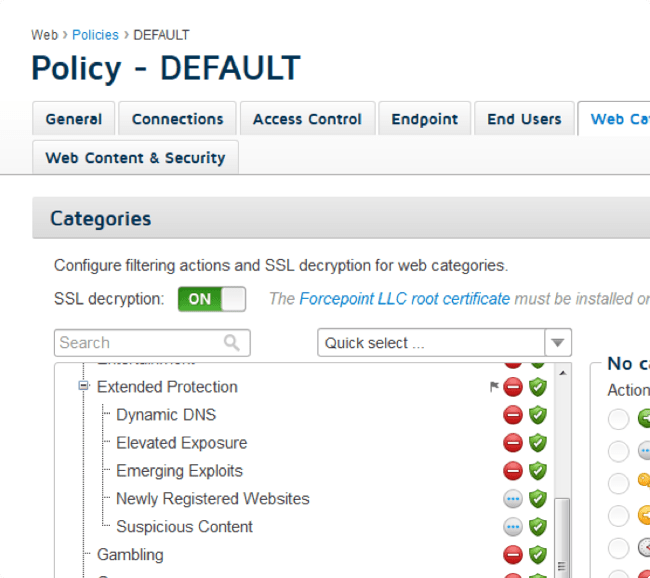
Consistent policies with robust access control for all your sites, cloud apps, and users — both on and off the corporate network.
Advanced threat protection powered by ACE
Keep users safe from malicious threats, including zero-day threats.
Industry's most secure cloud infrastructure
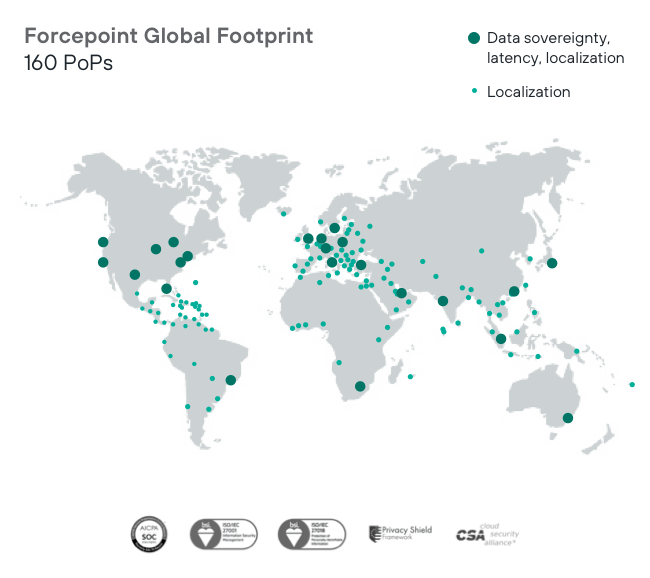
Global access points for faster local connectivity with over 160 PoPs across 145 countries.
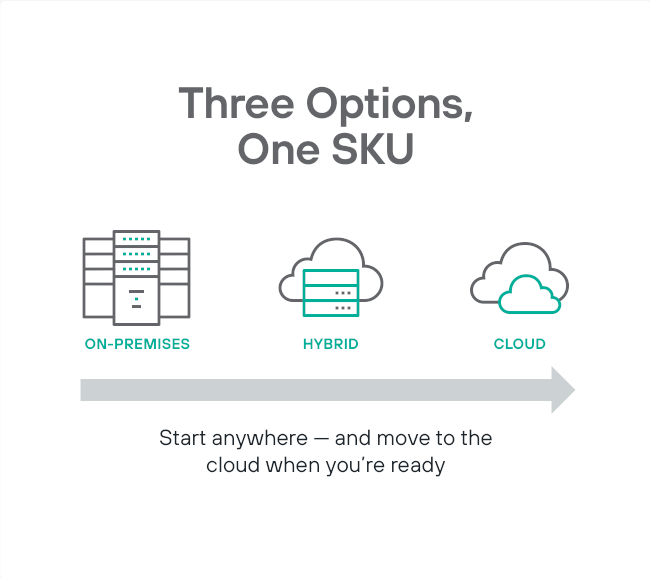
Move to the cloud at your own pace
Choose when, where and how you deploy. Choose where and how you connect to the cloud.
Web Cyber Security Guard VS. The Competition
Unified Endpoint with Dynamic Proxying
The convenience of securing your global workforce with a single endpoint for Web Security, DLP, CASB, and NGFW with flexible connectivity and traffic redirection options.
Deployment Flexibility
Deploy how, when and where you want. On-premises, hybrid and cloud deployment architectures so you can go to the cloud at your own pace.
Comprehensive Cloud Application Security
Monitor and control cloud app usage across your organization to uncover risk and eliminate security gaps.
Complete Data Protection
Protect your data on channels, devices, and applications - on the web, over email, at endpoints, on networks and in the cloud.
Advanced Threat Protection
Dynamic capabilities to keep your organization safe from a continually evolving threat landscape.